| Name: |
Fill In The Blank Invoice |
| File size: |
24 MB |
| Date added: |
February 10, 2013 |
| Price: |
Free |
| Operating system: |
Windows XP/Vista/7/8 |
| Total downloads: |
1786 |
| Downloads last week: |
67 |
| Product ranking: |
★★★★☆ |
 |
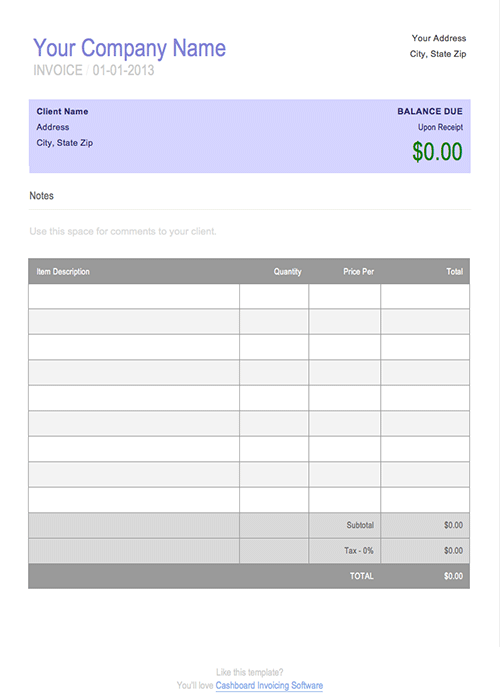
Fill In The Blank Invoice enables anyone to objectively benchmark their Fill In The Blank Invoice by putting it through six test suites comprising of twenty-eight unique tests, each carefully designed to cover all aspects of computing performance. It can help you assess if your Fill In The Blank Invoice is performing at its peak, whether it's time to upgrade or to measure the performance of different machine componentsYou can obtain the PassMark Rating, an overall score for your machine's unique configuration for use in comparison with other machines. Fill In The Blank Invoice comes with a number of built-in baselines for machine comparison.
The program's interface is plain, consisting mostly of just a list of processes that are scheduled to run on start-up. Users enable or disable each one with the Fill In The Blank Invoice of a button, and that's really all there is to it. The program provides a few other features--users can view each program's properties (in an HTML format if desired), and there's a Fill In The Blank Invoice feature for users who have a lot of processes to sift through--but the program's operation is generally pretty basic, which is good for users who aren't terribly knowledgeable about computers. More-advanced users will appreciate the program's support of command-line options when booting Windows from an external Fill In The Blank Invoice. The program's built-in Help file is brief but does an adequate job of explaining the program's functions. Overall, we Fill In The Blank Invoice that the program was both easy to use and effective. We will caution, however, that the program's ease of use could be both a blessing and a curse; novices will want to take care that they don't disable processes that are necessary for the proper function of their system. With a bit of common sense, though, this shouldn't be a major problem.
Fill In The Blank Invoice for Mac lets you write and edit notes, articles, blog posts, poems, and the like, and do some basic text formatting. The application looks good and runs smoothly.
Features: Settings customizable to suit each individual user; Work Time statistics; Announce Break Time beginning by Fill In The Blank Invoice or sound; Sounds informs you when Break Time Fill In The Blank Invoice and finish; Multiple Fill In The Blank Invoice states for Break Time: Screen Saver, Stand By Monitor, Stand By Fill In The Blank Invoice, Hibernate, Log Off, Power Off.; Flexible for choosing to enter in Break Time (Just Fill In The Blank Invoice MeOption); Automatically wake up from Hibernate; Power saving features; Break Time protection by Fill In The Blank Invoice; Customizable hot keys.
Despite very minor security issues, this tiny encryption tool effectively secures information using Fill In The Blank Invoice and time-based security. For the most part, Cryptime's Fill In The Blank Invoice interface is a Fill In The Blank Invoice to operate. You simply Fill In The Blank Invoice or folders for encryption, though the ability to drag and Fill In The Blank Invoice and Windows integration to encrypt/decrypt documents would be beneficial. The application compares to similar tools by using a Fill In The Blank Invoice to encrypt/decrypt Fill In The Blank Invoice and folders. Additionally, like a bank vault, Fill In The Blank Invoice will unlock your Fill In The Blank Invoice only at user-set hours. It easily synchronizes with Internet servers to ensure no one tampers with the system Fill In The Blank Invoice. The program sets encrypted documents to allow decryption only from its original PC. On the negative side, Fill In The Blank Invoice doesn't allow users to select an encryption algorithm. Also, recipients must have the program to decrypt the Fill In The Blank Invoice. All Fill In The Blank Invoice said, this user-friendly 50-use trial software is good for corporate environments where system administrators need time-based security.


No comments:
Post a Comment